Want to learn about Capture The Flag? The place where I begin my Capture The Flag journey ; Solving Challenges in CTFlearn(ctflearn.com)
I would not suggest you long list so that you get bored and not try it. I would like to share my experience stepping into CTF with a small step into a small CTF competition that I participated in and solved taking the time and gradually improved.
So here we go, I will be posting the challenges I solved from easy to hard. Every challenge that will be listed is in order from easier to more difficult. On that, we will have other blogs about medium and hard sections. So stay put and begin the journey of solving CTF with me.
The CTF challenge that I began with was https://ctflearn.com/. You can register here and begin with me. Don't hesitate to google and find help for every challenge. Try to understand the categories the challenge is focused on, try to learn about it by googling and joining the forums. It's the best way to get started.
There are mainly seven categories in the CTF as follows :
1. Web
2. Forensic
3. Programming
4. Binary
5. Reverse
6. Crypto
7. Misc
If you want to learn what these categories are, there are several articles which you can find easily on the Internet. So don't be a lazy bum get going !!
Ok now the solving of the easier challenges start now:
easy
WEB
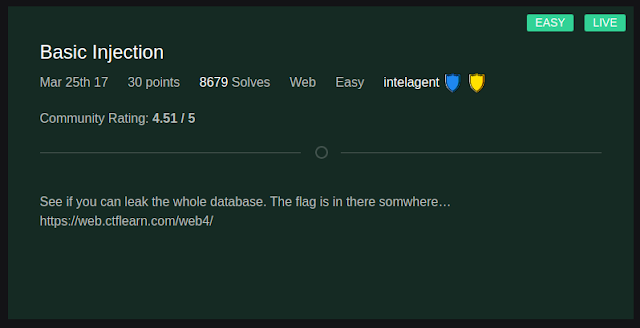
1. Binary Injection -web
This was the first challenge on the web which I solved using my prior knowledge and research of web challenges.
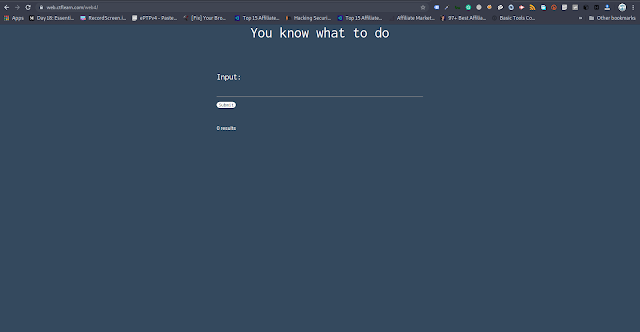
1. The was a link given in the challenge which will lead to a site with form as follows:
2. I tried giving a basic payload providing an apostrophe and semicolon one after another as it is the first thing you need to try when its challenge about SQL injection. Yeah, it did not work :). Therefore, I went for another basic payload i.e 'or1-'1 and submitted it which spit out the flag as follows:
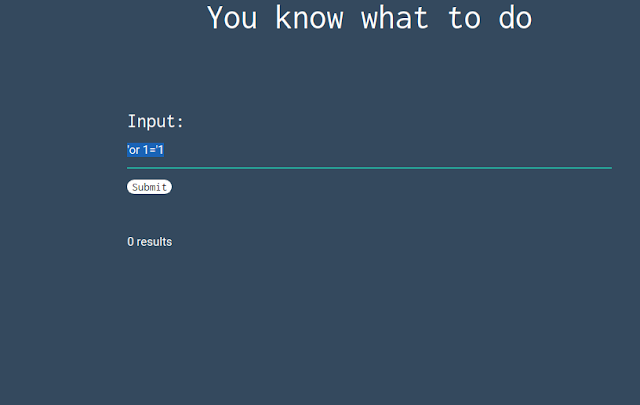 |
| The Payload which worked after I submitted and gave me the flag. |
 |
| The flag that I got after basic SQL injection payload. |
If you want to learn about SQL Injection you can see the OWSAP guide for SQL injection here: https://www.owasp.org/index.php/SQL_Injection.
I got the flag pretty easy as it was the easy section challenge on the challenge list.
Tips: While solving the web challenge please keep in mind the first things you need to do is, analyze the site with the following tools and techniques as a basic step:
This is my key idea to solve a web challenge and above mentioned are the basic tools that you can use to analyze a web challenge. you can dig deeper about the tools as well. Keep in mind these are just tips to get started there are lots of things you need to find out know about. Best place Google, Reddit, ctftime.org, etc.
flag: CTFlearn{th4t_is_why_you_n33d_to_sanitiz3_inputs}
Tips: While solving the web challenge please keep in mind the first things you need to do is, analyze the site with the following tools and techniques as a basic step:
- cURL
- Python
requestslibrary - SQL Injection
- brute force
- Burpsuit
flag: CTFlearn{th4t_is_why_you_n33d_to_sanitiz3_inputs}
Forensic
1.Forensic 101- Forensic
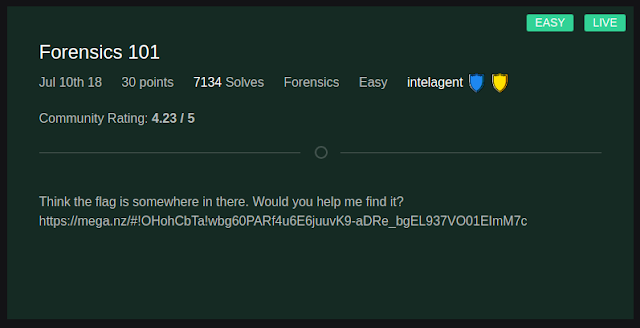 |
The first easy challenge in the forensic section was pretty straightforward to solve. There was a mega.nz link: https://mega.nz/#!OHohCbTa!wbg60PARf4u6E6juuvK9aDRe_bgEL937VO01EImM7c
where we had to download the file and find the flag.
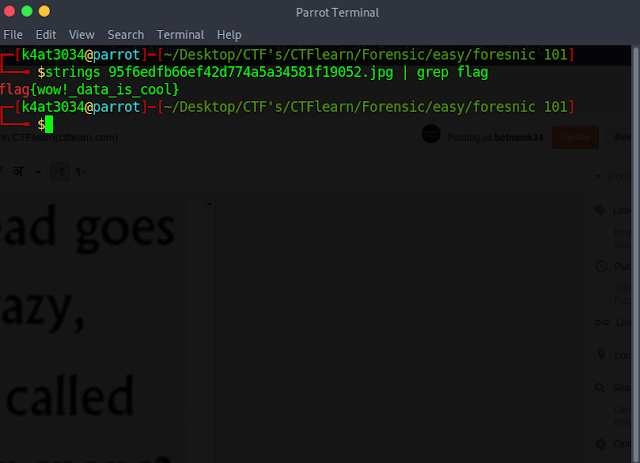
1. I went to the link and downloaded the file: 95f6edfb66ef42d774a5a34581f19052.jpg, a jpg file.
2. I used the display command to see the file it just showed me the following image which was of no help:
 |
3. So, sticking to the basics I opted to see the content of the file so I used cat command to view the content but still, no help. I went for the second option on my forensic tools i.e strings with grep command which gave me the following output with flag:
Tips: While solving the forensic challenge please keep in mind the first things you need to do is, analyze the file with following tools no matter what:
This is my key idea to solve a forensic challenge and above mentioned are the basic tools that you can use to analyze a forensic challenge. These are some tips to get started but not the solution for all forensic challenges you may encounter.
flag: flag{wow!_data_is_cool}
filestringscatgrepexiftoolbinwalkforemost
flag: flag{wow!_data_is_cool}
2.Taking LS- Forensic
This was the easy second challenge for the forensic section. This challenge also had a link to mega.nz: https://mega.nz/#!mCgBjZgB!_FtmAm8s_mpsHr7KWv8GYUzhbThNn0I8cHMBi4fJQp8
1. I downloaded the zip file from the link: The Flag.zip
2. Then unzipped the file using the following command on the file: unzip The\ Flag.zip
3. I checked for the extracted file with ls command which showed me __MACOSX & The Flag
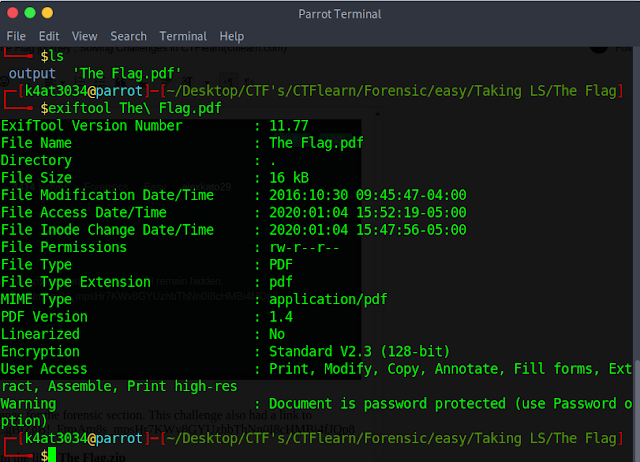
4. I checked every file inside both the folder with forensic tools which led me to a file named The Flag.pdf inside The Flag directory.
5. I tried to see the metadata of the pdf file using following exiftool command: exiftool The Flag.pdf which gave me the following output:
6. We could see the info of the pdf file and a warning saying it is password protected. Which made me think of what may be the password. Going through the rigorous searching I finally found that the hint on the challenge was the file will be still hidden, which made me think if what there were hidden files while I extracted the zip. so, I used ls -la command to see if there was a hidden file inside The Flag directory while extracting and boom!! I go the hidden file: folder named ThePassword
7. I look inside the folder there was a file inside named ThePassword.txt, I looked at the content of the file using cat ThePassword.txt which gave me the following output: Nice Job! The Password is "Im The Flag".
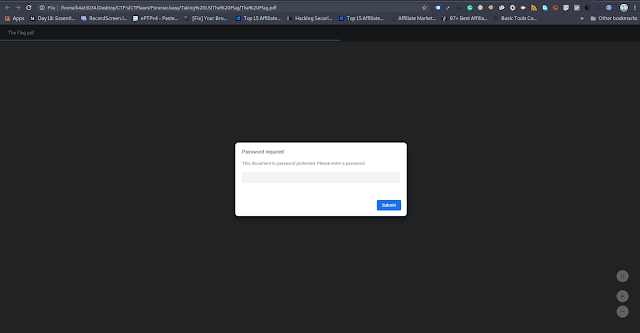
8. Now I got the password and started digging into finding the flag using various tools in the terminal wasting a lot of time. As a I was getting frustrated not being able to get the flag I thought of googling it and searching for the clue to solving the challenge. I came across a video explaining how to solve a pdf file with a password. The catch was I had to open the pdf in the browser and use the password.
9. I opened the pdf on the browser as follows which gave me the option to enter my password:
1. I downloaded the zip file from the link: The Flag.zip
2. Then unzipped the file using the following command on the file: unzip The\ Flag.zip
3. I checked for the extracted file with ls command which showed me __MACOSX & The Flag
4. I checked every file inside both the folder with forensic tools which led me to a file named The Flag.pdf inside The Flag directory.
5. I tried to see the metadata of the pdf file using following exiftool command: exiftool The Flag.pdf which gave me the following output:
6. We could see the info of the pdf file and a warning saying it is password protected. Which made me think of what may be the password. Going through the rigorous searching I finally found that the hint on the challenge was the file will be still hidden, which made me think if what there were hidden files while I extracted the zip. so, I used ls -la command to see if there was a hidden file inside The Flag directory while extracting and boom!! I go the hidden file: folder named ThePassword
7. I look inside the folder there was a file inside named ThePassword.txt, I looked at the content of the file using cat ThePassword.txt which gave me the following output: Nice Job! The Password is "Im The Flag".
8. Now I got the password and started digging into finding the flag using various tools in the terminal wasting a lot of time. As a I was getting frustrated not being able to get the flag I thought of googling it and searching for the clue to solving the challenge. I came across a video explaining how to solve a pdf file with a password. The catch was I had to open the pdf in the browser and use the password.
9. I opened the pdf on the browser as follows which gave me the option to enter my password:
10. I entered the password that I retrieved earlier and got the flag as follows, as the flag was in the form of content of pdf:
flag: ABCTF{T3Rm1n4l_is_C00l}
The third easy challenge in the forensic section where we had to download a file from the link:
https://mega.nz/#!qbpUTYiK!-deNdQJxsQS8bTSMxeUOtpEclCI-zpK7tbJiKV0tXYY
1. I downloaded the file from the link: PurpleThing.jpeg
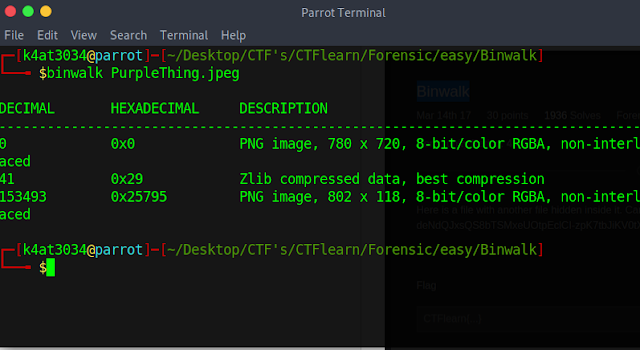
2. As the challenge topic is binwalk I binwalked the file: binwalk PurpleThing.jpeg which gave me the following output:
3. As per the binwalk info there are two png images and a zlib compressed file. Now I just used the -e flag to extract the files using the following command: binwalk -e PurpleThing.jpeg which extracted a folder named _PurpleThing.jpeg.extracted which had two files 29 and 29.zlib which was not the required file as the ouput must be two png images and a zlib compressed file.
4. Looking around the man page of binwalk tool and some goolgeling I found a solution to extract the file with -D flag which means we can extract a file with type signatures, where we can give the files an extension in which we want to extract. so, the command was:
binwalk -D 'png image:png' PurpleThing.jpeg
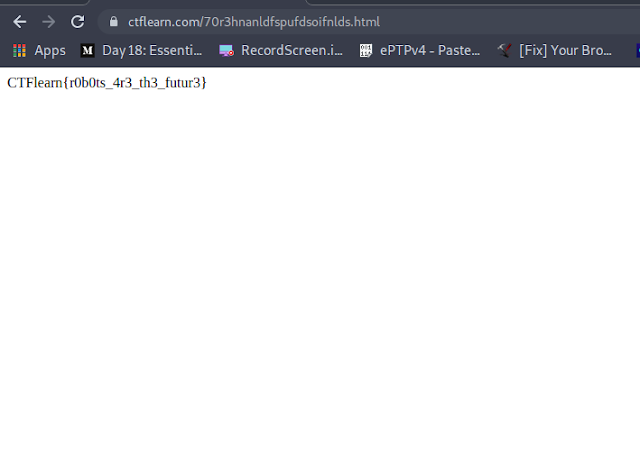
flag: CTFlearn{r0b0ts_4r3_th3_futur3}
3. Binwalk - Forensic
https://mega.nz/#!qbpUTYiK!-deNdQJxsQS8bTSMxeUOtpEclCI-zpK7tbJiKV0tXYY
1. I downloaded the file from the link: PurpleThing.jpeg
2. As the challenge topic is binwalk I binwalked the file: binwalk PurpleThing.jpeg which gave me the following output:
4. Looking around the man page of binwalk tool and some goolgeling I found a solution to extract the file with -D flag which means we can extract a file with type signatures, where we can give the files an extension in which we want to extract. so, the command was:
binwalk -D 'png image:png' PurpleThing.jpeg
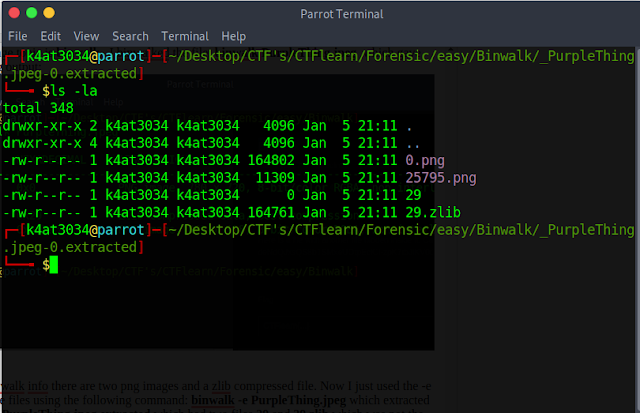
5. Wallha!!!! the command extracted a folder named _PurpleThing.jpeg-0.extracted which contained our necessary files as follows:
6. Now time for finding the flag checked 0.png with display command it was the same image which you could see when displaying the main image, PurpleThing.jpeg. So second go, viewing the second image with display 25795.png gave us the flag as follows:
If you want to know about the binwalk tool in Linux please check:https://tools.kali.org/forensics/binwalk
flag: ABCTF{b1nw4lk_is_us3ful}
Miscellaneous
1. Where Can My Robot Go? - Miscellaneous
This challenge was the easier first challenge listed in the miscellaneous section. As per the hint, for the challenge to do find about robots, I knew there was something to do with the robots.txt file for the site.
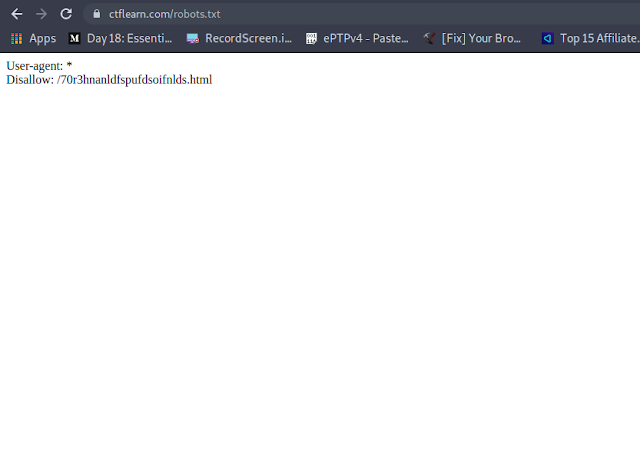
1. I checked for the robots.txt file on the portal going to the URL: https://ctflearn.com/robots.txt which gave me another hint about another disallowed folder in there as follows:
2. So I browse to the folder going to the disallowed folder going to URL: https://ctflearn.com/70r3hnanldfspufdsoifnlds.html and got the flag for the challenge:
flag: CTFlearn{r0b0ts_4r3_th3_futur3}
2. Practice Flag - Miscellaneous
This was pretty easy as it was just for the practice. You just need to input the given flag and submit it.
flag: flag{CTFLearn_is_awesome}
3. Reversal of fortune - Miscellaneous
This challenge was also pretty easy. As per the instruction, the flag was the handle name of the hacker. you could easily reverse read the intercepted message. But I wrote a simple python code so I could do the same in future challenges.
Intercepted message: .nac uoy fi tIe$reveRpilF eldnah ym gnisu em egassem ,avaj yllacificeps ,gnidoc emos htiw pleh deen I ,deifitnedi tegrat txeN
Python script:
when I ran the script it gave me the handle name which was the flag:
flag: FlipRever$eIt
4.Wikipedia - Miscellaneous
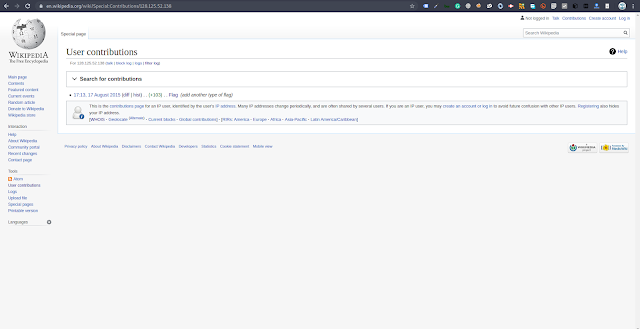
The fourth challenge in the miscellaneous section was quite confusing as there was only a hint saying Wikipedia and some port number is going to help find the flag. So believing n my intuition went to the Wikipedia page and searched for the port number which resulted in the following search:
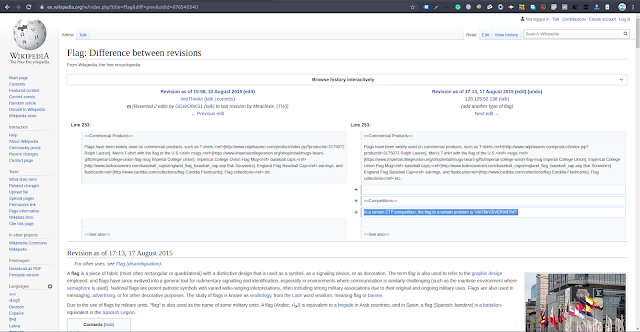
There was nothing much but just clicking through the hyperlinks I landed to the following page when I clicked diff just after the date which I suppose was the flag. Luckily it was the flag.
The flag was just in the hint saying: In a certain CTF competition, the flag to a certain problem is "cNi76bV2IVERlh97hP".
flag: CTFlearn{cNi76bV2IVERlh97hP}
Crypto
1. Character Encoding - Crypto
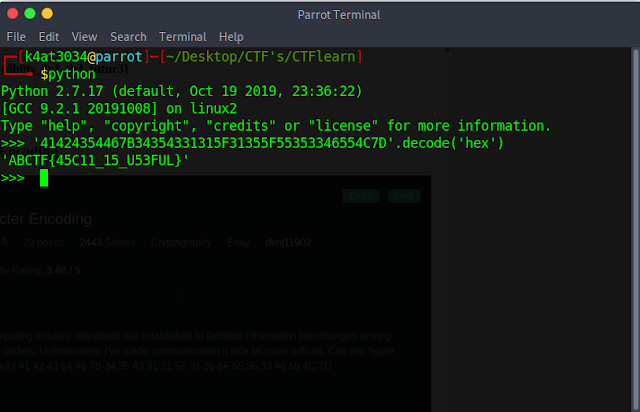
The first challenge in the crypto section was pretty easy and straight forward. we just need to decode the Hex encoded string to ASCII.
hex-encoded string: 41 42 43 54 46 7B 34 35 43 31 31 5F 31 35 5F 55 35 33 46 55 4C 7D
1. Opened the python terminal and just did the hex decryption and got the flag:
flag: ABCTF{45C11_15_U53FUL}
flag: 0xc0ded
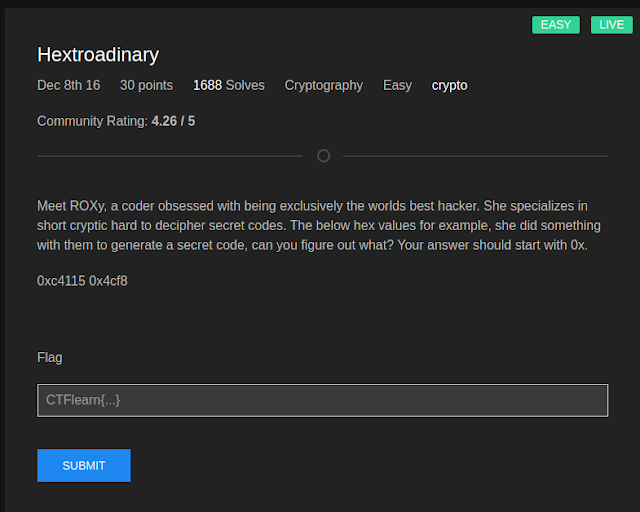
2. Hextroadinary - Crypto
The second challenge in the crypto section made me think for a while. Going through the description of the challenge the hacker ROXy meant there was something to do with XOR and the code was hex values. Therefore to my prior knowledge, the code is generated through the calculation of two hex values so I opted for hex calculator and got the flag which I joined with the hint of flag starting with 0x:
flag: 0xc0ded
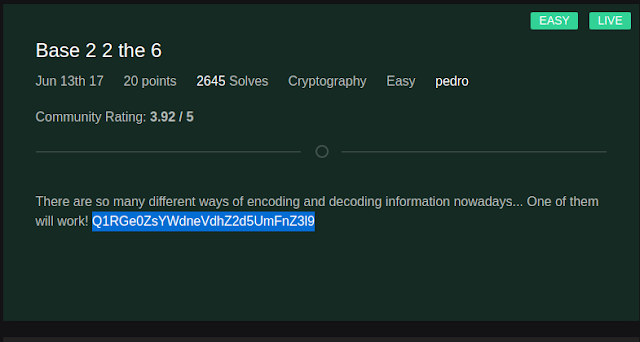
3. Base 2 2 the 6
The third challenge in the crypto section was quite easy as per the topic of the challenge was Base 2 2 the 6 and the challenge was to decrypt a encoded string:
Q1RGe0ZsYWdneVdhZ2d5UmFnZ3l9
As the topic of the challenge said base 2 2 the 6, I assumed it to be base 64 encodings as 2 to the power 6 is 64 and it turned out to be true as I decode the string with base64 in python I got the flag.
More solutions for other challenges will be listed here. Please stay tuned and follow me on twitter: k4at3034: https://twitter.com/k4at3034. Your suggestion is kindly accepted for further improvements. Please support by clicking the Ads :P. ThankYou










Comments
Post a Comment