HSCTF 8 -2021
I started ctf after quiet a while, and saw HSCTF 8 going on I could solve few challenges but would like to share the way i solved 1 web, and 6 misc which I will tell you how I solved it. here we go.
NRC:
In this challenge you could not right click and inspect as the right click was disabled in js. The walk around was you just need to press CTR + U to view the source , after you land the source page you could find a suspicious bootstrap file , you just click the file to view and you could find the flag for the first web challenge.
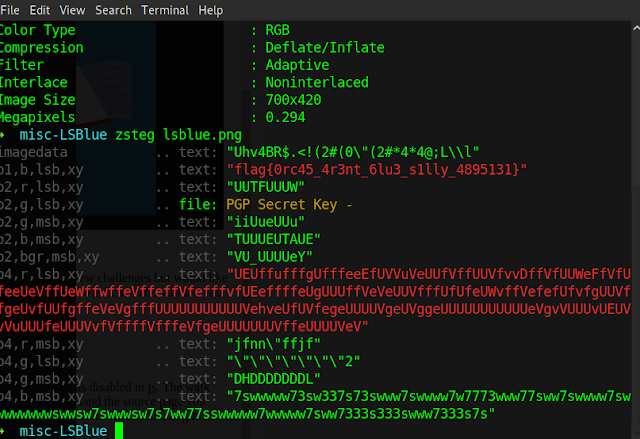
misc-LSBlue:
This challenge was pretty forward as as per my prior knowledge when its a .png file i will want to use few choice of my tools to do the stegno challenge. So i used to zsteg out of the list and got the flag. you can use anything of your choice
misc-pallets-of-gold:
This challenge was also pretty forward, i used stegsolve to find the flag. I opened the file in stegsolve and started going through different channel one after another. I could visualize something on the image when i reached channel green plane 1,the flag hidden on the image could be seen clearly as follows:
Thank you guys i could only solve few challenges , other challenges in misc were pretty simple like filling up survey, finding flag in discord and all. so i was placed 579th this time playing alone, hope to improve in next ctf. If you want to join me and create a team my ctftime team name is :r00tn3p@!.
WeCTF 2021
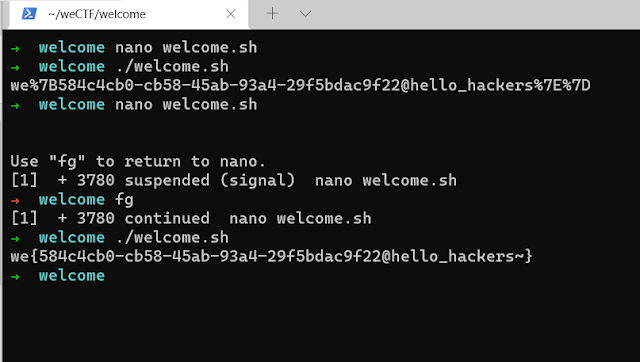
welcome:
The challenge was pretty simple, you were given a base64 encoded string and you just need to decode it. I did decode the base64 string but the output was URL encoded so I had to decode the URL encoded string and got the flag: we{584c4cb0-cb58-45ab-93a4-29f5bdac9f22@hello_hackers~}
Here are some screenshot of things I did to solve including the shell script I developed for future reference.
shell script :
first step:
second step:
Include:
This challenge was pretty straight forward as per the heading and its hint of flag being in flag.txt file on the server. This was the case of LFI (local file inclusion), I was lucky enough t get the flag in my first go of disclosing information with directory traversal attack, which is one of the first test you can perform in case of LFI.
flag: we{695ed01b-3d31-46d7-1413-06b744d20f4b@1nc1ud3/etc/passwd_yyds!}
payload: http://include.sf.ctf.so/?🤯=../../../flag.txt
I tried to put one '../' at a time in front of flag.txt and finally got the flag when I added the third.
So, I could not check out other challenges in this years WeCTF 2021 because of office work but it was really fun getting those 2 flags. Hope i can participate next year and solve more flags.
guys you know what to do to support me :), I don't need to tell you. A little support can make this guys day. like and share my blog if you think its helpful.
stay calm and play CTF.






Comments
Post a Comment