TUCTF 2019 Writeups
Challenge: Red Yarn - misc
We were provided with the following pop-up while clicking the challenge in the misc section.
As we could see there was a file named DEBUG.COM that could be downloaded and some description saying we need to go back to the basics. The first thing I did was download the file and saved it. As always I change the permission of the file using chmod o+x DEBUG.COM. After that performed the following steps one after another until I got the flag.
1. Used file command to see the file type which gave me information saying it was DOS executable file which was of no help.
2. I used strings command on the file (strings DEBUG.COM)which gave me the file, maybe I was lucky as I was sticking to the basics :).
flag: TUCTF{D0NT_F0RG3T_TH3_B4S1CS!}
Challenge: Super Secret- misc
We were provided with the following pop-up while clicking the challenge in the misc section.
As we could see the file had .odt extension it must be an OpenDocument text file. So as I downloaded the file, changed the permission (chmod o+x document.odt)and performed the file command in the downloaded file (file document.odt) which gave me the following output in the terminal:
and I was right about the extension. performed cat on the file which was of no use, again sticking to the basics I performed strings on the file which gave me the following output:
which had nothing interesting apart from the lines Basic/Standard/flag.xmlU and Basic/Standard/flag.xmlPK.
As we know word document structure is like many file in a zip. I tried to unzip the .odt (unzip document.odt) file, which gave me the following documents and files:
So now we have all the files and folders unzipped from the documents.odt file and we know the hint that flag.xml is inside Basic folder I performed grep inside the Basic and found the flag as follows:
flag: TUCTF{ST0P_TRUST1NG_M4CR0S_FR0M_4N_UNKN0WN_S0URC3}
and I was right about the extension. performed cat on the file which was of no use, again sticking to the basics I performed strings on the file which gave me the following output:
which had nothing interesting apart from the lines Basic/Standard/flag.xmlU and Basic/Standard/flag.xmlPK.
As we know word document structure is like many file in a zip. I tried to unzip the .odt (unzip document.odt) file, which gave me the following documents and files:
So now we have all the files and folders unzipped from the documents.odt file and we know the hint that flag.xml is inside Basic folder I performed grep inside the Basic and found the flag as follows:
flag: TUCTF{ST0P_TRUST1NG_M4CR0S_FR0M_4N_UNKN0WN_S0URC3}
Challenge: Open Door -web
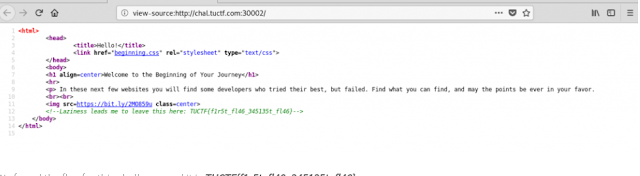
This CTF was pretty simple as I went to the link chal.tuctf.com:30002 it gave me the following page:
maybe I was lucky, I performed the basic steps in web challenges i.e view-source and inspect. Here i viewed the age source and got the flag which was in the comment section :P.
flag: TUCTF{f1r5t_fl46_345135t_fl46}
I downloaded the file and performed file command on the file which gave me the info it was ELF file which was of no help.
so I performed a cat on the file with grep command which was still of no help as well. Sticking to the basic I performed strings on the file with grep ( strings runme | grep "TUCTF") which gave me the flag as follows:
flag: TUCTF{7h4nk5_f0r_c0mp371n6._H4v3_fun,_4nd_600d_luck}
As I could only solve few challenges in TUCTF 2019 I will be posting writeups that I solved and few others which I didn't, by reading the writeups of other participants so that I could look back and see for hints in further CTF challenge. You can read the writeups and start your journey of CTF.
Challenge: Run Me-PWN
so I performed a cat on the file with grep command which was still of no help as well. Sticking to the basic I performed strings on the file with grep ( strings runme | grep "TUCTF") which gave me the flag as follows:
flag: TUCTF{7h4nk5_f0r_c0mp371n6._H4v3_fun,_4nd_600d_luck}
As I could only solve few challenges in TUCTF 2019 I will be posting writeups that I solved and few others which I didn't, by reading the writeups of other participants so that I could look back and see for hints in further CTF challenge. You can read the writeups and start your journey of CTF.













Comments
Post a Comment